Gutsy Redefines the Security Governance Market with Process Mining
More tools don’t equate to better security
John Morello | September 14, 2023
The Tools Dilemma
On average, organizations deploy more than 30 security tools, collectively costing tens of millions of dollars. Yet, despite this significant investment, many security teams continue to grapple with fundamental challenges, such as timely patching of vulnerabilities, effective incident containment, and efficient identity management.
The problem doesn't lie in the number or quality of tools you possess. It's in their orchestration and integration with your existing processes and teams.
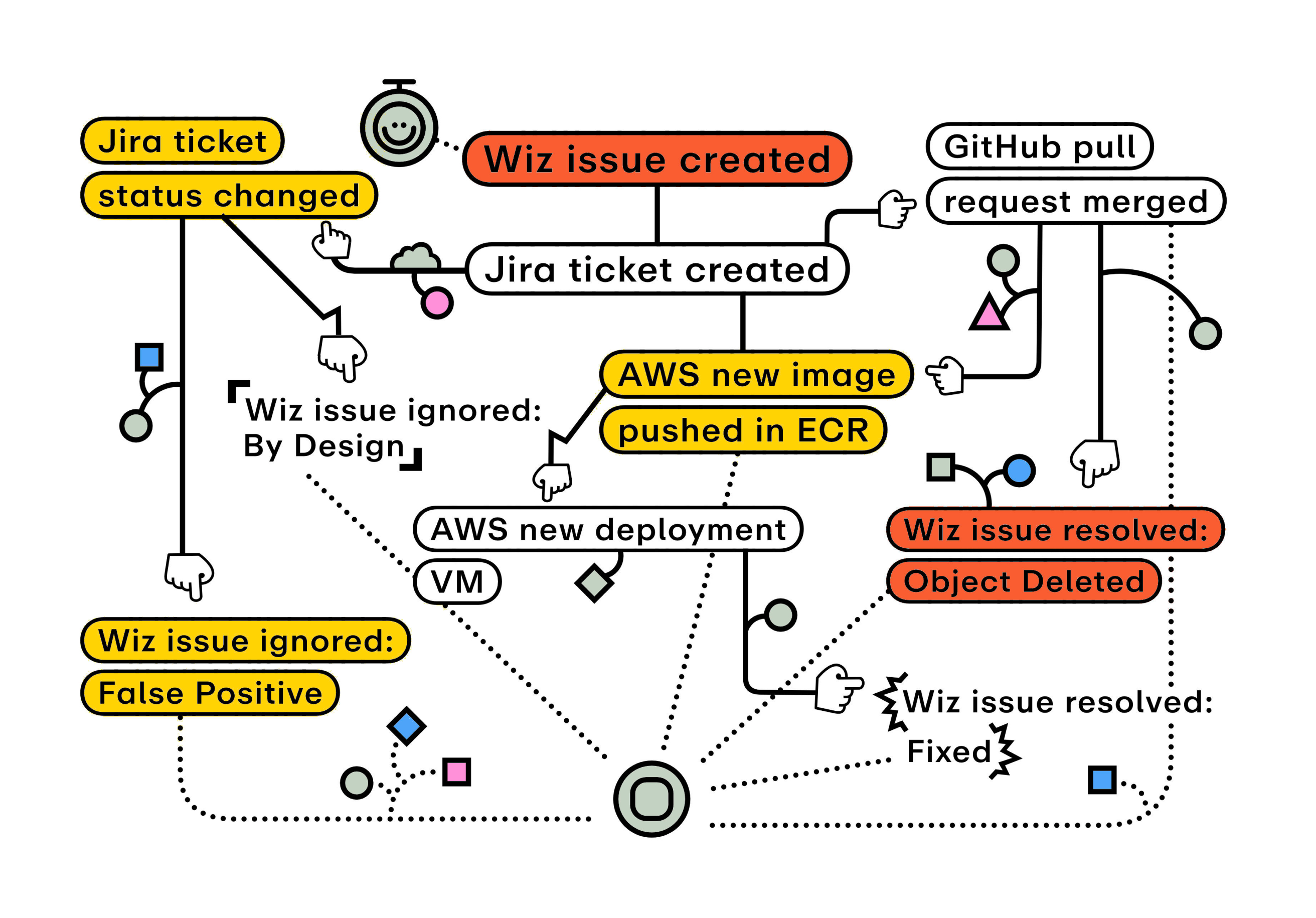
Gutsy’s Innovative Solution
Our comprehensive view of your security-related processes unveils each step, handoff, and execution involved in your cybersecurity practices. Gutsy’s process data mining seamlessly connects with existing systems, removing man from machine. Manual data is never imported into the analysis. This not only reduces manual effort, it is critical all ingested information are actual, observable events to avoid any human misunderstandings or biases. This ground-breaking data collection makes Gutsy the only way enterprises can truly eliminate bias, assumptions, and guesswork from their security governance equation. The result is unassailable insights for optimizing your security processes and verifying the effectiveness of your invested security tools.
Process Data Mining at Its Best
Gutsy continuously gathers real-time events and automatically correlates complex workflows across all your security tools and platforms. This revolutionary approach provides you with an unprecedented level of insight into how your processes genuinely function. You can delve deep into the details, understanding not only the outcomes but also the hows and whys behind them.
Download our eBook, “Process Mining: The Security Angle” to see why more enterprises are putting Gutsy in their cybersecurity arsenal:
Download eBook