Freeze Your Process Data: Simplified Auditing and Zero-Impact Experimentation
Introducing Point-in-Time Snapshots
Jacob Graves | February 5, 2024

Getting continuous visibility into your security processes is incredibly powerful, but with great power comes new challenges. How can a security leader pull accurate data about the efficacy of their processes when those processes happen continuously? How can you explore and experiment with your process data without impacting the workflows you’ve built on your live system?
In Gutsy’s newest release, we’re introducing snapshots. No more exporting data to spreadsheets just to have consistency. Now, you can take a snapshot of any live process directly in Gutsy, and use the snapshot to explore and examine your process data without impacting your live systems.
Why it Matters
Security activity happens continuously and around the clock. Unlike deployments, which can be paused for audits or delayed for business reasons, security activity like patching and incident response never ends. This becomes a problem when security leaders look to pull data on their security processes.
Whether you’re pulling data for audits, a board meeting, or a work presentation, continuously evolving data sets can pose an enormous challenge. In the past, you may have been forced to export all data from a system to do reporting, losing all the interactive elements of the system itself.
With Gutsy’s new ability to snapshot processes, security leaders now have a frozen data set to inspect, classify, and tag. This simplifies management tasks such as reporting on your past performance or satisfying auditors' requests.

Snapshot Features
A security process can be long-running. Sometimes, when things go wrong, they can take weeks or months to close out.
Frozen Data for Audits
Auditors inspect these security processes to prove that security teams are doing an acceptable job at protecting the business. Most auditors look at specific time windows, such as a year or a quarter. Once they start gathering data, they don’t want to see that data change since it's the basis for their assessment. Live processes in Gutsy are continuously updating with the latest information, so auditors might find a case they’re inspecting is updated during their assessment.
With snapshots, you can freeze the data, making a point-in-time copy, so auditors have a consistent platform to prepare their reports. Since snapshots still live in Gutsy, you can use all the rich features in the Data Viewer and Process Map, including deep filtering and tagging, on a stable data set without seeing changes from the live data.
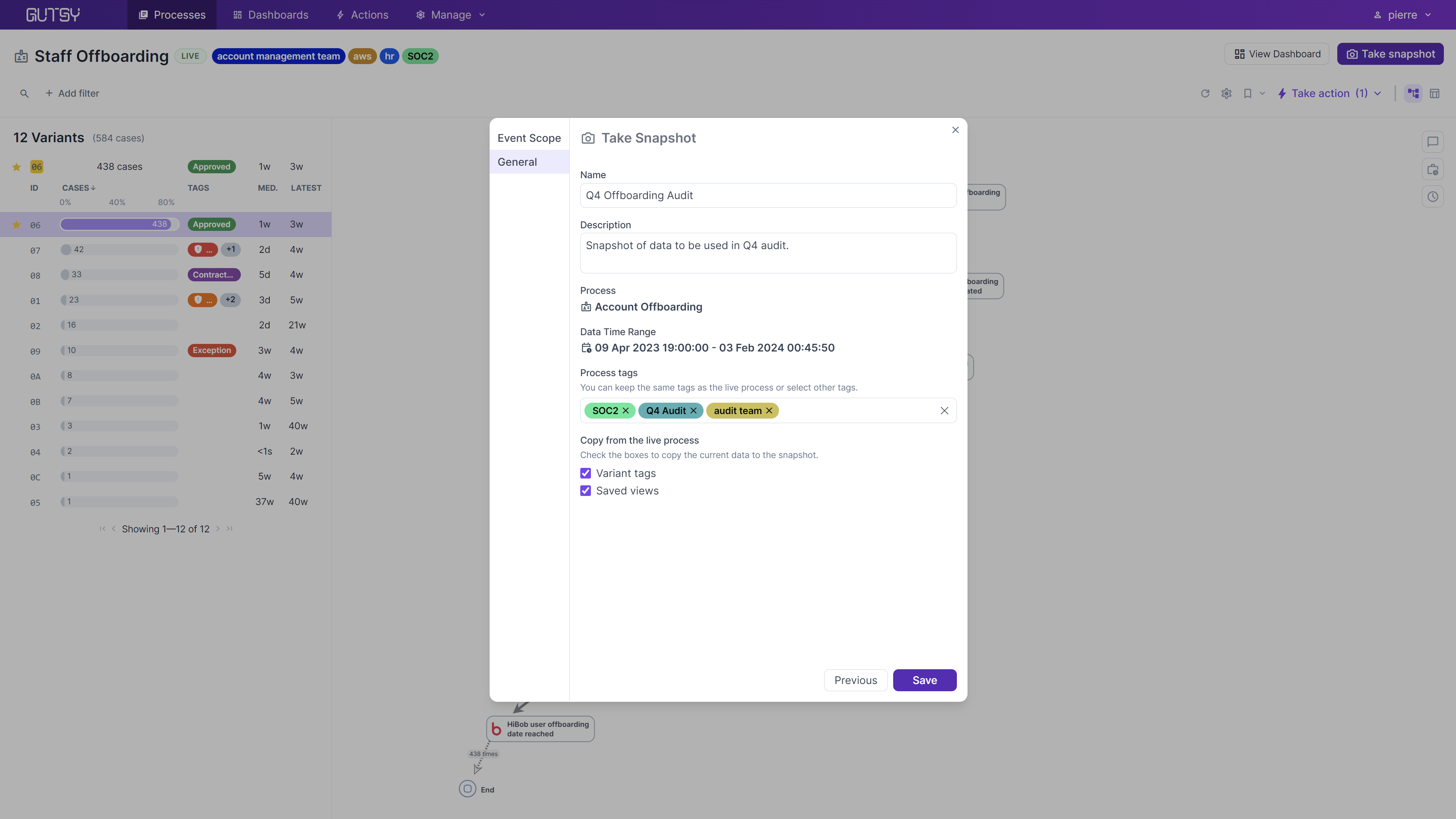
Separate Tags and Filters
Even after you create a snapshot, the process display is fully interactive. Filters and tags are specific to the snapshot, and kept separate from the parent live process. In your live process, you might use tags to identify risks and inefficient variants; in the snapshot, you might use tags to keep track of the variants you have finished auditing and which are still to be worked. You might save a filtered view to narrow down your snapshot data further to focus your audits on particular trouble spots.
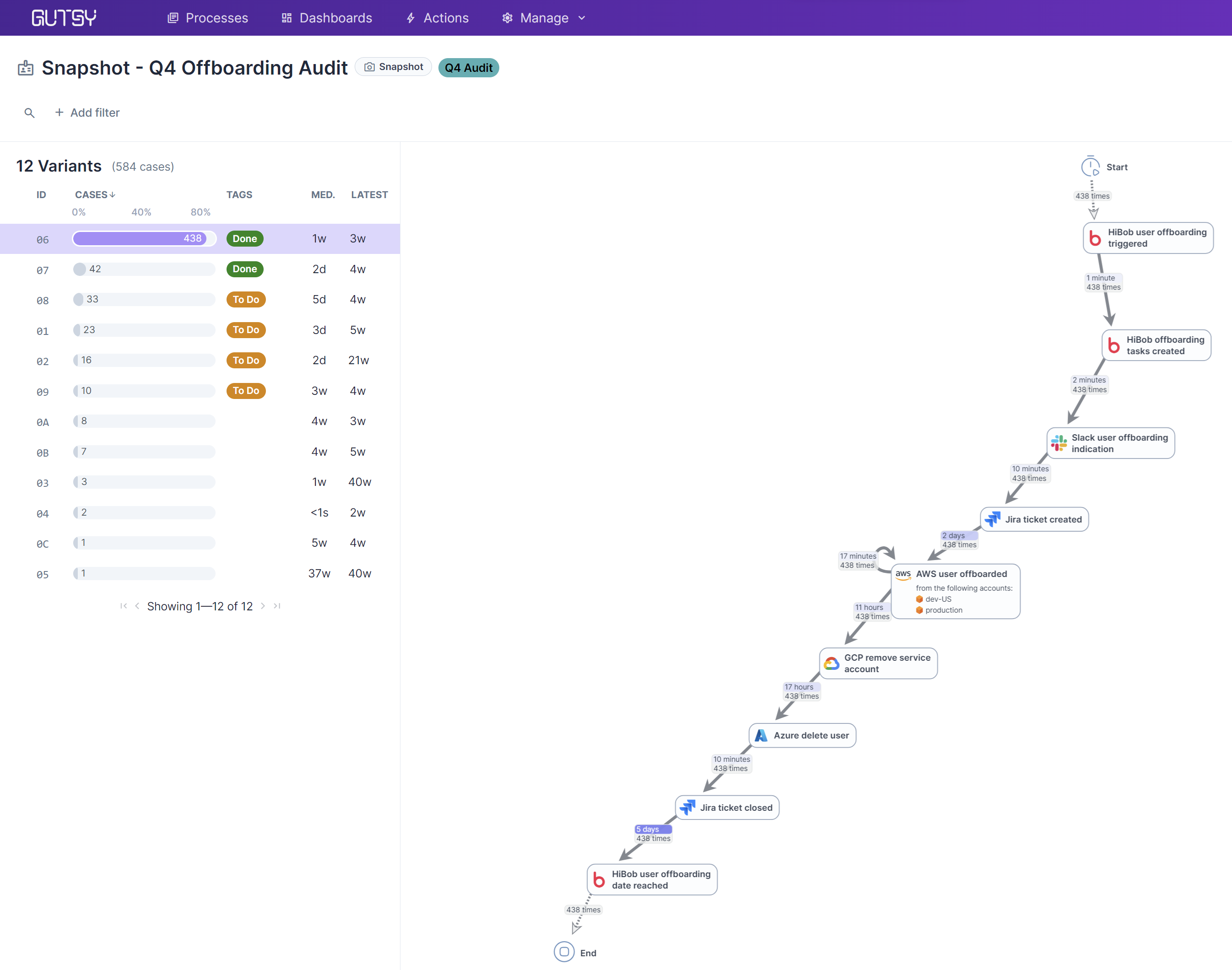
Playground for Experimentation
Sometimes, security leaders want to play with their data to answer “What if?” questions. What if we tagged each process with an owner? What if we automated a specific step? What if we want to prepare for some upcoming changes that can’t yet be shared with the team? Snapshots offer a safe sandbox to slice-and-dice your data without disrupting or affecting your live process. Since snapshots can be created in just a few clicks, it’s easy to create one just to play around with and better understand the intricacies of your security practices.
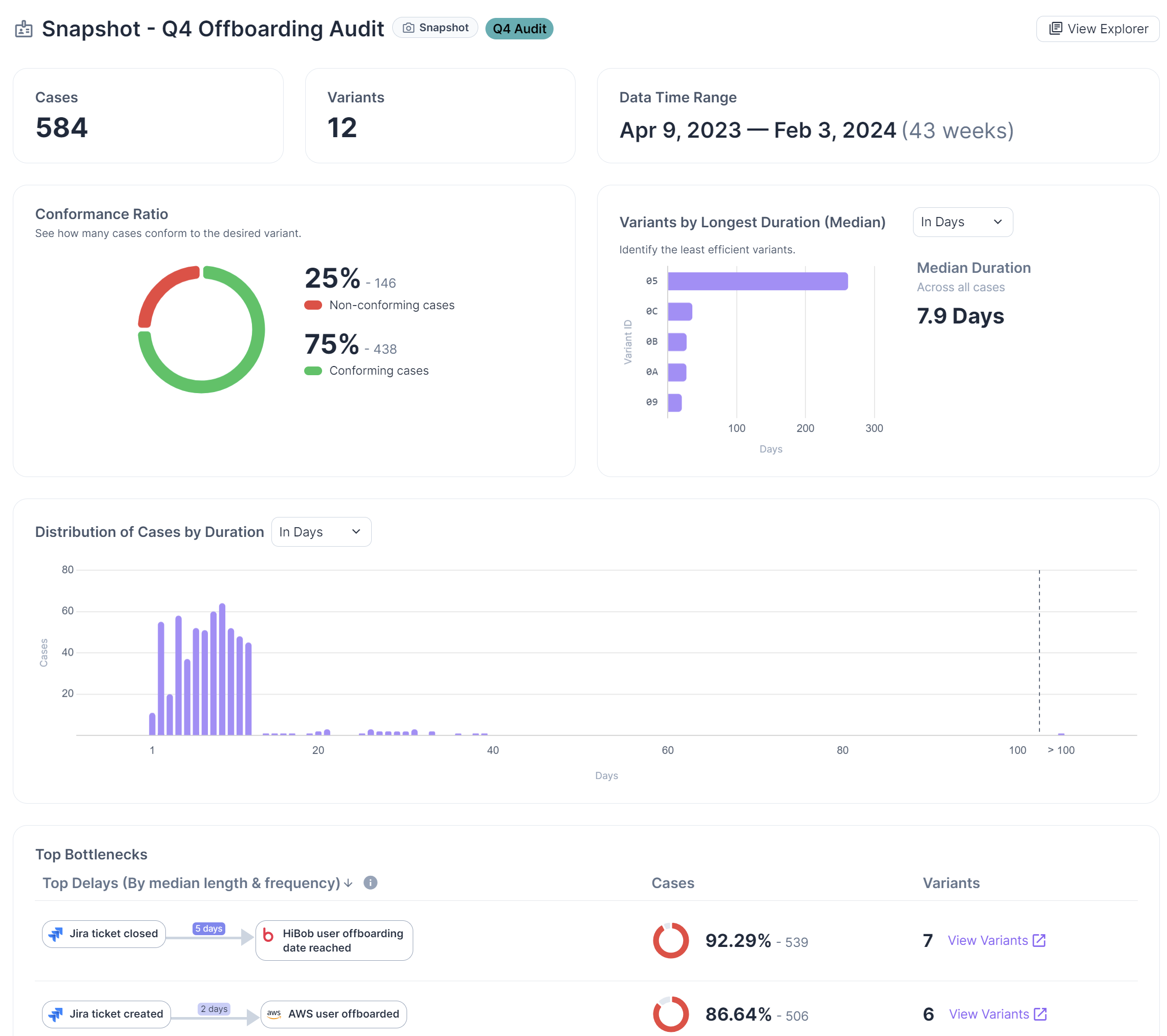
Snapshot Dashboards
Just like live processes, snapshots also have dedicated dashboards that track process KPIs and serve as reference points to show improvement over time. Whether you are seeking data to support your assertions in board presentations, all-hands team meetings, or quarterly security updates, snapshot dashboards will provide helpful visuals and extensive metrics.
Let us show you this new snapshot capability in action so you can better understand how our process mining for cyber solution will transform your security governance strategy, reduce legal liability and speed up your security outcomes.