“Who did what?” Find Answers that Matter with Gutsy's New Data Viewer Feature
Gain actionable insights with a seamless integration into existing security infrastructures
Aqsa Taylor | December 5, 2023

Introducing Data Viewer
You know your process failed, but where do you go from there? With Gutsy’s new data viewer you can not only see what went wrong in your process but drill down into exact specifics from each case.
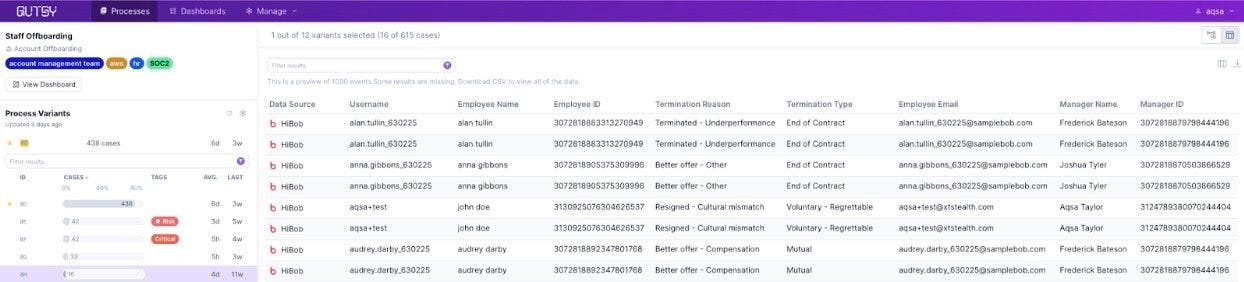
How it works
Gutsy collects metadata from different systems in order to identify each process execution. For example:
- A vulnerability management platform involving a vulnerability scanner
- A ticketing platform
- A development pipeline
In theory, changes should be merged each time the vulnerability remediation process is triggered.
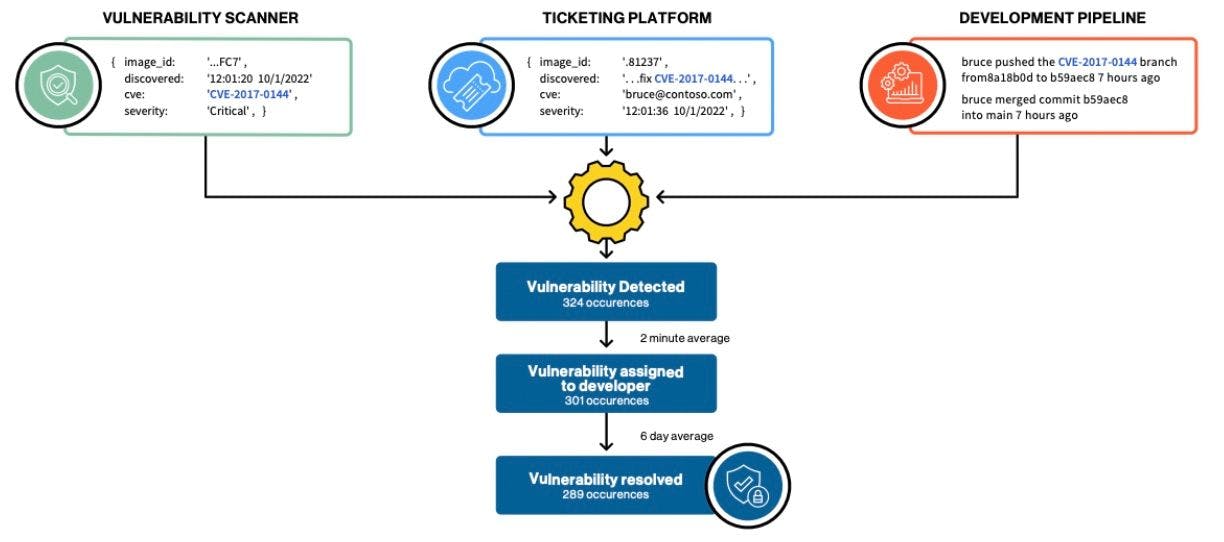
Gutsy’s data viewer complements the process map, offering a complete breakdown of the data for each case and process execution. Whereas the process map aims to simplify the data and construct a coherent image that summarizes the details, the data viewer does the opposite. It offers an alternative view, with a direct window into the particulars.
With the data viewer, you can scan the exact details for every event to learn more about the data layers that are excluded from the process map, such as the people behind the events, the exact CVE numbers, the timestamps, and more. The data is provided in a convenient table format, with autocomplete filters for seamless investigation.
Real Use Case
Consider an organization that requires removing access from AWS, Azure and GCP cloud platforms as part of their offboarding process for dev team members. In most cases, the organization removes access to the employee from both dev and production accounts.
However, in some cases, access is only removed from production accounts and not development accounts, leaving residual access for terminated and potentially disgruntled employees.
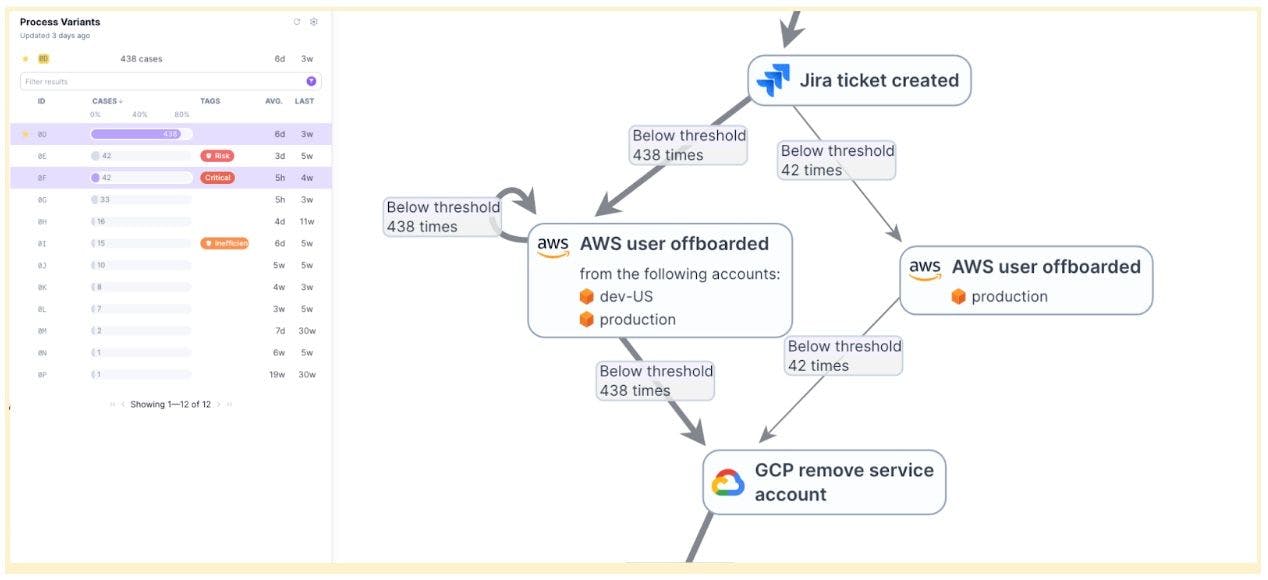
In the above example, we see a process inconsistency with sporadic access removal. Sometimes access is removed only for the AWS production account, other times access is removed for both the AWS dev-US and production accounts.
In order to remove residual access, the team must first know which employees still have access to the AWS dev-US accounts. Then they can remove that access before it leads to intentional or unintentional compromise of credentials.
With Gutsy, the process of discovery is nearly immediate. Simply go from the process map view to the data viewer, and filter the data.
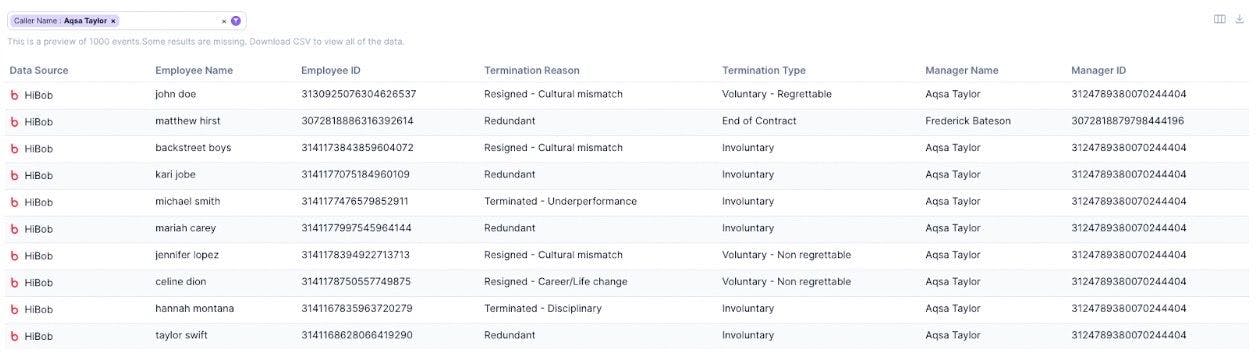
With the data at their fingertips, security teams can use Gutsy’s powerful filtering capabilities to identify and remediate process failures, by knowing exactly what to fix, where to turn to, and who to involve.
This is only one of the many ways Gutsy’s new data viewer can equip security teams with actionable insights. For a detailed discussion of how process mining works, how it can be applied to security, and what benefits it delivers to security leaders, book a free demo: